Table Of ContentMoving Away from Collision Avoidance:
Towards Collision Detection in Wireless Networks
Souvik Sen Naveen Santhapuri
DukeUniversity DukeUniversity
Romit Roy Choudhury Srihari Nelakuditi
DukeUniversity UniversityofSouthCarolina
ABSTRACT
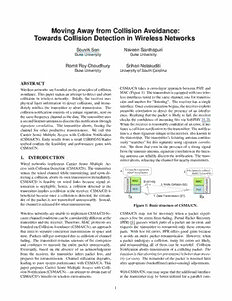
CSMA/CN takes a cross-layer approach between PHY and
Wirelessnetworksarefoundedontheprinciplesofcollision
MAC(Figure1). Thetransmitterisequippedwithtwowire-
avoidance. Thispapermakesanattempttodetectandabort
lessinterfacestunedtothesamechannel, onefortransmis-
collisions in wireless networks. Briefly, the receiver uses
sion and another for “listening”. The receiver has a single
physical layer information to detect collisions, and imme-
interface. Oncecommunicationbegins,thereceiverexploits
diately notifies the transmitter to abort transmission. The
preamble correlation to detect the presence of an interfer-
collisionnotificationconsistsofauniquesignature,senton
ence. Realizingthatthepacketislikelytofail, thereceiver
thesamefrequencychannelasthedata.Thetransmitteruses
checks the confidence of incoming bits via SoftPHY [1,2].
asecondlistenerantennatodiscernthisnotificationthrough
Whenthereceiverisreasonablyconfidentofanerror,itini-
signature correlation. The transmitter aborts, freeing the
tiatesacollisionnotificationtothetransmitter. Thenotifica-
channel for other productive transmissions. We call this
tionisashortsignatureuniquetothereceiver,alsoknownto
Carrier Sense Multiple Access with Collision Notification
thetransmitter. Thetransmitter’slisteningantennacontinu-
(CSMA/CN). Early results from a small USRP/GNURadio
ously “searches” for this signature using signature correla-
testbed confirm the feasibility and performance gains with
tion. We show that even in the presence of a strong signal
CSMA/CN.
fromthetransmitantenna,signaturecorrelationatthelisten-
ingantennacanreliablydiscernthenotification. Thetrans-
1. INTRODUCTION
mitteraborts,releasingthechannelfornearbytransmitters.
Wired networks implement Carrier Sense Multiple Ac-
cesswithCollisionDetection(CSMA/CD).Thetransmitter
senses the wired channel while transmitting, and upon de-
tectingacollision,abortsitsowntransmissionimmediately.
CSMA/CD is feasible on wired links because signal at-
tenuation is negligible, hence, a collision detected at the
transmitterimpliesacollisionatthereceiver. CSMA/CDis
beneficial because once a collision is detected, the remain-
der of the packet is not transmitted unnecessarily. Instead,
thechannelisreleasedforothertransmissions.
Figure1: BasicstructureofCSMA/CN.
Wireless networks are unable to implement CSMA/CD be- CSMA/CN may not be necessary when a packet experi-
causechannelconditionscanbeconsiderablydifferentatthe encesafewbiterrorsfromfading. PartialPacketRecovery
transmitterandthereceiver. Therefore, MACprotocolsare (PPR) [1] guesses which parts of a packet are in error, and
foundedonCollisionAvoidance(CSMA/CA),anapproach requests the transmitter to retransmit only these erroneous
thataimstoseparateconcurrenttransmissionsinspaceand parts. With few bit errors, PPR offers good gains because
time. Packetsstillgetcorruptedduetocollisionorchannel it avoids an entire packet retransmission. However, when
fading. The transmitter remains unaware of the corruption a packet undergoes a collision, many bit errors are likely,
and continues to transmit the entire packet unnecessarily. and retransmitting all of them can be wasteful. Collision
Eventually, based on the absence of an acknowledgment Notification aborts transmission of a colliding packet. The
from the receiver, the transmitter infers packet loss, and intuitionisthataborting(orprevention)isbetterthanrecov-
prepares for retransmission. Channel utilization degrades, ery(orcure). Theremainderofthepacketisresumedlater
leading to poor system performance with CSMA/CA. This afterappropriate(backoff/rate/carrier-sensing)adjustments.
paper proposes Carrier Sense Multiple Access with Colli-
sionNotification(CSMA/CN)–anattempttoobtainpartof WithCSMA/CN,onemayarguethattheadditionalinterface
CSMA/CD’sbenefitsinwirelessenvironments. at the transmitter may be better utilized for a parallel com-
1
munication, perhapsonadifferentchannel. Weclarifythat
the“listener”maynotbeviewedasanadditionalinterface,
only a simple correlation logic with an antenna. Decoding
capabilities are not necessary, hence, this logic can be part
of the same interface. Besides, collision notification to the
listenerisin-band,requiringnoadditionalbandwidth.
Figure2: CSMA/CNframeformats.
Thispapermakesthreecontributions:
(1)IdentifyingamiddlegroundbetweenCSMA/CDandCA.
withR’sreception,causingpacketcorruption(Figure3). To
CSMA/CN is an early attempt to rethink medium access
detectsuchcollisions,receiverR“searches”foraPHYlayer
control in wireless networks. This paper explores the first
preamble in its incoming signal. Searching occurs through
steps in this direction, demonstrating that further develop-
correlation of the preamble with the signal arriving at R’s
mentsarefeasibleandworthpursuing.
antenna. This happens in parallel, and does not affect the
normalpacketdecodingprocedure.OnceT1’spreambleim-
(2) Develop the Collision Notification architecture with
pingesonR’santenna,thecorrelationexhibitsaspike,rais-
practical constraints in mind. Our designs are validated
inganalertthatthepacketmaybein“trouble”. Ofcourse,
with supporting measurements on the USRP/GNURadio
arrivalofanewpreamblemaynotnecessarilycauseacolli-
platform. We show the feasibility of detecting collisions at
sion;thereceptionmaysometimessucceedeveninpresence
thereceiver,aswellasreliableidentificationofthecollision
of the interference. To verify the impact of interference, R
notificationatthetransmitter’slisteningantenna.
consultsSoftPHY[1]toobtainconfidencevaluesofthebits
arrivingfromT.Theconfidencevalueisanindicatorofhow
(3) Implement and evaluate CSMA/CN on a prototype of
likelyabitisinerror. Basedonawindowofconfidenceob-
seven USRP nodes. Experimental results show consistent
servations,Risabletoinferwhetherthepacketisexpected
throughputimprovementsover802.11andPPR.Weidentify
to get corrupted. If so, R halts reception, and prepares to
severalavenuesoffurtherresearch.
sendacollisionnotificationtotransmitterT.
2. ARCHITECTUREANDDESIGN
We believe that any attempt to abort collisions in wireless
links will need to conform to the following functional re-
quirements. (1) A wireless transmitter T cannot detect the
collision while transmitting; the receiver R must get in-
volved. (2) Receiver R will need to detect collision and
convey it back before the packet is fully transmitted. (3)
T needs at least an additional antenna for listening while
Figure3: Rcorrelatestopreamble,denotedCorr(Pre).
transmitting. This section proposes CSMA/CN as a prac-
tical system that conforms to these requirements. Design IftheinterfererT1startsfirst,andthetransmissionfromT
decisions are discussed next followed by feasibility tests. starts later, R may need to abort T (Figure 4). However,
Later,Section3presentstheoveralltestbedresults. R must first ensure that the later-arriving signal is actually
meant for itself. Preamble correlation is not sufficient be-
(1)Design: TransmissionandCollisionDetection causeT mayusethesamepreamblefortransmittingtosome
InCSMA/CN,thetransmitterT usesoneinterfacefortrans- otherreceiver;Rshouldnotsendanabortthen. Becauseof
mittingandtheother(correlator)forlistening. Thereceiver this, R “searches” for its own signature in the signal. If T
R uses its single interface for multiplexing between trans- intendsitstransmissiontoR,itwouldembedR’ssignature
missionandreception. TransmissionisinitiatedasinIEEE in the packet. R will detect this through signature correla-
802.11, except one difference: for every packet, the PHY tion,andsendoutanabort. Tosummarize,Rsearchesfora
layer preamble is concatenated with an additional bit se- preamblewhilereceivingitssignalofinterest,butsearches
quence, a signature, uniquely computed from the intended foritsownsignaturewhilereceivinganinterference.
receiver’sidentifier(Figure2(a)). ThetransmitterT ensures
thechannelisidleandtransmitsthispacketusingthetrans-
mitantenna. Thelisteningantenna, byvirtueofbeingvery
close to the transmitting antenna, receives this signal with
a high signal strength – we call this the self-signal. The
packet’s intended receiver R also receives the transmitted
signalandstartsdecodingthearrivingbits. Simultaneously,
Rtriggerscollisiondetection.
Figure4: Underinterference,Rcorrelatesitsownsigna-
Collision happens when a nearby transmitter T1, interferes
ture,denotedasCorr(Sign(R)).
2
(2)Design: CollisionNotificationandAbort Algorithm2: R.receive()
The Collision Notification (CN) is composed of only the 1: ifFrameofinterestisalreadybeingreceivedthen
receiver R’s own signature. This is the same bit sequence 2: ifCorr(Preamble)highandmanybitssuspectthen
thatT includedinitspackettoR(Figure2(b)). Thereceiver 3: Transmit<Sign(R)>
transmitstheCNpacketlikearegular802.11ACK–thereis 4: ifInterferingframeisbeingreceivedthen
nocarriersensing,hence,theCNistransmittedeventhough 5: ifCorr(Sign(R))highthen
the transmitter is still transmitting. The listening interface 6: Transmit<Sign(R)>
of the transmitter continuously correlates for the receiver’s
signature in the incoming signal (Figure 5). This correla-
tion is more challenging because the self-signal is much (3)SupportingMeasurements: SignatureCorrelation
stronger than the notification. We show that even then the Weemphasizethatsignaturecorrelationdoesnotrequirede-
listenercandiscernthenotificationwithconsistentaccuracy. codingthesignaturebits–itsufficestoonlydetectthesig-
nature’s presence in the channel. Systematic experiments
Upon discerning the notification, the listener immediately undervaryingnetworkconditionsshowthatsignaturecorre-
alertsthetransmittinginterface,whichthensuspendstrans- lationcanberobust. Figure6(a)showsthenoticeablejumps
mission (other transmitters like T1 do not abort because incorrelationwhenaknownsignaturearrivedamidcontin-
theyarenotcorrelatingwithR’ssignature). Thecorrectly- uousbackgroundtransmissions.
abortedtransmitterbacksoffasprescribedin802.11. Other
backlogged nodes in the vicinity takes up this opportunity
e 3e+09
totransmit;ifnoothernodetransmits,thesametransmitter alu 2.5e+09 10 byte signature (SINR = -10dB)
V
mayresumetransmission. n 2e+09
elatio 1 .15ee++0099
Corr 5e+0 08
0 10000 20000 30000 40000 50000
Sample Number
25
Signature size 5 bytes
Signature size 10 bytes
20 Signature size 20 bytes
o Signature size 30 bytes
ati
R
n 15
o
Figure5: T abortsduetosignaturecorrelation. T1con- ati
tinuesbecauseitissearchingforR1’ssignature. el 10
orr
A pertinent question is whether the collision notification C 5
will interfere with nearby active transmissions. This will
certainly be true when the interferer’s receiver is close to 0
-25 -20 -15 -10 -5 0 5 10
the notification sender. Nevertheless, the small size of the
(Known signal) - (background signal) (dB)
notificationpermitsvariouspossibilitiesforefficientrecov-
ebfaredy.rineWpgalhioreesnds.ibtSyiunactehsrcfaheresemcsh,eetmlhikeeesehPmoPrpRtlo,wyaiesnddifotowitscooafpsebmiwtaeliltrhrboufrarssdtcinaongf on of false +/- 000 .0.0.0012...515253 FFaallssee npeogsaittiivveess
cthaenphaacnkdeltemearryobrsedauugemtoenntoetdifiwciatthiojnusatsenwoeulgl.hAerlrtoerrncaotrivreeclyt-, Fracti -0.0 05-20 -15 -10 -5 0 5 10
Signal strength difference with interferer
ing codes to recover from the notification-sized errors [3].
Finally,observethat802.11ACKscanalsoinduceerrorsat Figure 6: (a) The correlation value spikes every time a
anearbyreceiver,muchlikeCSMA/CN’scollisionnotifica- known signature arrives amid a background transmis-
tions. Theyonlydifferinthekindoftopologiestheyimpact. sion. (b) Correlation Ratio with varying transmitter-
receiverseparationandsignaturesize. (c)Falsepositive
We believe CSMA/CN is a simple but novel approach to and false negative rates of discerning collision notifica-
wirelessmediumaccesscontrol. Thefollowingpseudocode tionagainstvaryingtransmitter-receiverseparation.
capturesthecoreflowofoperations.
To quantify the jumps, we define Correlation Ratio as the
Algorithm1: T.transmit(R,Data)
correlation observed once the signature arrives, divided by
1: Begintransmittingframe<Preamble:Sign(R):Data> theaveragecorrelationbeforeitsarrival. Figure6(b)shows
2: KeeplisteningandcorrelatingwithSign(R) the variation of Correlation Ratio with increasing RSSI
3: ifCorr(Sign(R))highthen difference between the signature and background transmis-
4: Aborttransmission sions. Put differently, in the lower end of the x-axis, the
signature is much weaker than the background signal, as
3
can be expected when the collision notification arrives in questions: What is the (1) accuracy and delay of detecting
presenceoftheself-signal. Evidently,performanceissatis- a collision at the receiver? (2) turn around time from col-
factory so long as the signature is no weaker than 18dB of lision detection to transmission abortion? (3) CSMA/CN’s
theself-signal. Figure6(c)showsthefalsepositiveandfalse throughputgainoverPPRand802.11?
negativeratesofsignaturecorrelation. Resultsarecertainly
promising. Inoursectiononongoingwork,wewilldiscuss To evaluate the accuracy and delay of collision detection
methodsofimprovedcorrelationforweakerlinks. at the receiver, we set up a transmitter-receiver (T-R) pair,
andamovinginterfererwithbackloggedtraffic. Allpackets
We also studied whether different notification signatures are 1500 bytes. The T-R link delivers almost 100% of the
mayinducesimilarcorrelations. Figure5showsascenario packetsinabsenceoftheinterferer. Inpresenceofinterfer-
where R’s signature arrives when T1 is searching for R1’s ence, the packet is either received correctly, received with
signature. To ensure that T1 does not abort, CSMA/CN errors, or not received at all (preamble corrupted). Figure
needs to ensure that the two signatures do not exhibit a 7(a) shows the break-up of these three cases with increas-
highcorrelation(nofalsepositives). Weinvestigatethisby ing SINR on the X-axis. CSMA/CN’s collision detection
cross-correlating randomly chosen 10-byte signatures. Ta- accuracycurveisalsoshown. Evidently,whentheSINRis
ble1showshighdifferencesbetweenauto-correlation(table low,CSMA/CNcanaccuratelyidentifyacollisionatthere-
diagonal) and cross-correlation. The values in the braces ceiverthroughpreamble-correlationandSoftPHYhints(re-
denotetheminimumhammingdistancebetweensignatures call scenario in Figure 3). The accuracy decreases when
i and j. Although promising, we plan to better understand the interference becomes much weaker than the signal – in
howthisscalestomoresignatures. such cases, SoftPHY is sometimes unable to recognize the
collision(falsenegatives). However, duetotheweakinter-
Table1:Correlationwithdifferentsignatures(minimum ference, the packet is correctly decoded 93% of times, and
HammingDistanceshowninparenthesis) hence, the impact of false negatives is marginal. We also
Sign. 1 2 3 4 5 observednegligiblefalsepositives(1%)intheexperiments.
1 5.8(0) 1.2(37) 0.9(42) 1.1(34) 1.3(37)
2 1.1(37) 4.1(0) 1.1(39) 1.7(32) 1.1(39)
Correctly decoded
3 1.3(35) 1.3(34) 5.1(0) 1.3(34) 1.4(34) Preamble decoded but packet lost
Preamble lost
4 1.2(34) 1.6(32) 0.9(42) 7.3(0) 1.2(37) ets Accuracy
k
5 1.1(37) 1.2(39) .9(39) 1.1(37) 5.0(0) pac 1
of 0.8
n
o
3. IMPLEMENTATIONANDEVALUATION cti 0.6
a
Fr 0.4
We have implemented CSMA/CN on a USRP testbed of
0.2
7 nodes. We used the GNURadio framework with Zigbee
0
CC2420asthephysicallayer. CC2420operatesat2.4GHz 0 1 2 3 4
with a symbol rate of up to 2M symbols/s, translating to a SIR in dB (SNR S - SNR I)
maximum of 250 Kbps. The Zigbee nodes perform carrier
senseandbackoff. TheSoftPHY,signaturecorrelation,and
collisiondetectionlogicwereportedtoZigbee. TheZigbee
implementationusesaharddecisiondecoder. Onthetrans-
mitter side, every 4 data bits (nibble) is mapped to a 32 bit
codeword. Hence there are 16 valid codewords. For every
32 bits received from the demodulator output, the receiver
maps it to the closest valid codeword. The Hamming dis-
tance between the received codeword and the closest valid
codewordprovidesSoftPHY’sconfidenceofthenibble.
We implement signature correlation using a matched filter.
WeuseathresholdontheCorrelationRatio–whenthesig- Figure7:(a)Collisiondetectionaccuracywithincreasing
nature correlation is above the ratio, the node identifies the interferencestrength(b)CDFofbyteswhenthecollision
arrivalofanewtransmission. Thethresholdischosenbased wasdetectedafteritstarted
on the RSSI difference between the self-signal and the re- CSMA/CN initiates the abort notification only after an in-
ceiver’ssignal(detailsomittedintheinterestofspace). Sig- terfering preamble is detected and the SoftPHY hints have
naturesizesarechosentobe5bytes. confirmed the collision. This operation introduces a delay.
Figure7(b)showstheCDFofthisdelay(expressedinnum-
3.1 PerformanceEvaluation
ber of bytes). Evidently, all the collisions were detected
Our experiments are designed to answer 3 performance within 16 bytes from the time of preamble detection. The
4
medianisaround7bytes,afairlysmallvalueincomparison ke 1.5
to a typical packet size. We conclude that CSMA/CN can 11-li CCNN @@ 255000KK ssaammpplleess ppeerr sseecc..
detectcollisionreasonablyquicklyandaccurately. 02. 1.4 CCNN @@ 12000000KK ssaammpplleess ppeerr sseecc..
8 PPR @ 250K samples per sec
The next experiment compares CSMA/CN’s throughput ver 1.3
o
against PPR [1] and the conventional scheme (we call it ut
p 1.2
802.11-like). We set up 3 USRPs, two collocated as the T
d
tlrinanks.mTiwttoeroathnedrolinneksatatrheeseretcuepivaerro,utondfothrmeCthSeMCAS/MCNA/lCinNk malize 1.1
– one acts as a hidden terminal link and the other an ex- or 1
N 0 .1 .2 .3 .4 .5 .6 .7 .8 .9 1
posed terminal link. These secondary links comprise of 2 Loss ratio of the weak link
USRPs each, hence, do not perform collision notification
themselves.Instead,theyactasinterfererstotheCSMA/CN 1
link, and contend and transmit on the “free” channel when
s 0.8
theCSMA/CNtransmissionisaborted. Inotherwords,their ket
c
throughput reflects the gains from CSMA/CN. Figure 8 re- pa 0.6
portstheaggregatethroughputoverallthree3links,against n of
increasing failure rate at the CSMA/CN link. The failure ctio 0.4
rateisincreasedbymovingthehidden/exposedlinkscloser Fra 250K samples per sec.
0.2 500K samples per sec.
to the CSMA/CN link. The results are averaged across 10 1000K samples per sec.
2000K samples per sec.
different topologies, and normalized over the 802.11-like 0
0 100 200 300 400 500 600 700 800 900 1000
scheme. As one may expect, CSMA/CN’s gain increases
Delay in bytes
withhigherpacketfailures. Inthisregime,largeportionsof
the packet are unnecessarily transmitted (and later retrans- Figure 8: (a) Performance gains with CSMA/CN and
mitted) with PPR. Aborting this redundant transmission PPR over packet receivers (b) CDF of notification over-
upfrontoffersbenefits. headforCSMA/CNinbytes
The turn around time (i.e., the time from the first bit error betweentransmissions. Thisemulates(althoughwithsome
to the time when transmission is halted) is of interest. A approximation) what would have happened if CSMA/CN
shorter turn around time (TAT) implies potential for larger wasrunningonthesamenetwork.
gains. Figure 8(b) shows the CDF of TAT in the units of
USRP byte-transmission time (we do not report absolute
1
timebecauseUSRPunitsincurartificialdelaysatthetrans- 802.11-like
PPR
mitandreceiveend,hence,theabsolutetimeismisleading). 0.8 CSMA/CN
Evident from the figure, the median turn around time is nks
around 150 bytes. This is somewhat large due to the artifi- of li 0.6
n
o
cthiaeludseelrayspiancoeb.tWaineinargeseaxmpplolerisnfgrotmhetphoesUsiSbRiliPtiefrsoonft-iemnpdlteo- Fracti 0.4
mentationinanFPGA/hardware. 0.2 802.11-PlPikRe
CSMA/CN
0
Tracebasedevaluation 0 5 10 15 20 25 30 15 20 25 30 35 40 45 50 55
Throughput in Kbps Throughput in Kbps
We use trace based evaluation to understand CSMA/CN’s
performance in a multi-link topology. The traces were Figure9:(a)CDFofthroughputinKbpswhereallnodes
collected from 5 different topologies, each with 5 USRP arecontinuouslyactive. (b)CDFofthroughputinKbps
transmitters scattered around 2 USRP receivers. Each re- withfixedsizetraffic(likeFTP).
ceiver was positioned to be in the range of 2 to 4 senders. Figure 9(a) plots the CDF of the throughput achieved by
Thelinksweremadereasonablystrong,hence,fadinglosses each link across all our experiments. This experiment was
werenegligible. However,withmultiplesenderscontending performed with continuous traffic from all transmitters.
for the channel, hidden and exposed terminals were nat- WhilePPRoutperformsthe802.11-likescheme,CSMA/CN
urally present. Two types of traffic patterns were used – performsevenbetter. Thisisexpectedbecausethenetwork
one continuous and another bursty, with a constant packet is collision dominated, hence, aborting a failed transmis-
size of 1000 bytes. We emulated the three protocols of- sion (prevention) is better than recovering from a failure
fline(CSMA/CN,PPR,and802.11-like)onthesecollected (cure). Althoughoverallthroughput improves, wefindthat
traces. Briefly,whenacollisionisobservedatalink(based theweakerlinksinCSMA/CNdonotbenefit(thelowerend
on the CSMA/CN criteria), our emulator stops that link, of the CSMA/CN CDF). This is because the weaker links
and starts the next transmission earlier. Carrier sensing, are continuously interrupted by interference, and hence,
backoff, and SIFS time slots are carefully accounted for canneverprogresssufficiently. WeverifythisthroughFig-
5
ure 9(b), in which transmitters have bursts of traffic. The Detecting Collisions: Authors in [9] enables a transmit-
stronger links finish their chunks quicker, allowing for the ter to distinguish between a fading and collision by having
weakerlinkstoadvancewithoutinterruption. the receiver return the received bits. SoftRate [2] utilizes
SoftPHY information to distinguish between collision and
4. LIMITATIONSANDON-GOINGWORK
fading for rate adaptation. In contrast, CSMA/CN detects
Improved Correlation: We observed that signature corre- andabortscollisionsonthefly.
lationisreliablewhenthecollisionnotificationisnoweaker
than 18dB compared to the self-signal. This could be a AbortingCollisions:Theonlyschemethatbearssomesim-
limitationofCSMA/CNsincecollisionmaybemorelikely ilaritywithCSMA/CNis [10]. Authorsuseanoutofband
(hence detection/abortion more vital) when the receiver is control channel to transmit pulses for the purpose of indi-
farawayfromthetransmitter. Weareexploringapproaches cating active transmissions. Transmitters sense the control
that can subtract the known self-signal, and apply the cor- channel to detect potential collisions, however, such deci-
relation on the residue. While this may appear to require sionsatthetransmitterarenotanaccurateindicatorofcol-
complexinterferencecancellation[4],asimpleandapprox- lisionatthereceiver. Weuseanin-band collisiondetection
imatemodelingofself-signalmaysufficeaswedonotneed scheme at the receiver with explicit feed back to the trans-
theactualbitsofthenotificationsignature. mittertoabort. Tothebestofourknowledge,thisisthefirst
prototype implementation of an in-band scheme for detect-
Multiple Interferers: Our accuracy of collision detection ingandabortingcollisions.
through preamble correlation is done in a setting with only
one interferer. We believe that preamble correlation works 6. CONCLUSIONS
well even in the presence of multiple interferers as it has
This paper proposes CSMA/CN to show that it is feasible
showntobefeasiblein[5]. Weplantoverifythisfurther.
and beneficial to abort an unsuccessful transmission with
theaidofacollisionnotificationfromthereceiver. Thear-
DecodableFeedbacks:InthecurrentversionofCSMA/CN,
chitecture is simple, while the additional hardware require-
the collision notification is unable to convey more than a
ments are minimal. Several facets of CSMA/CN still need
yes/no information. Additional information from the re-
tobethoroughlyexploredthroughextensiveimplementation
ceiver(suitablebitrate,causeoffailure,etc.) couldcertainly
andexperimentationbeforeitcanbeconsideredaviableal-
help the transmitter in deciding the appropriate response to
ternative to CSMA/CA. Nevertheless, we believe this work
the collision. Preamble correlation is inadequate to convey
presentsapreliminaryyetpromisingfirststepinwhatcould
such feedback. One option for the receiver is to time the
evolveintoanewtechnologyforfuturewirelessnetworks.
CN frame such that the transmitter can abort its transmis-
sion, and then start receiving the feedback information in 7. REFERENCES
theclear. Weareinvestigatingthemeritsofthispossibility.
[1] K.JamiesonandH.Balakrishnan,“PPR:Partial
PacketRecoveryforWirelessNetworks,”inACM
5. RELATEDWORK
SIGCOMM,August2007.
Avoiding Collisions: There have been numerous MAC [2] M.Vutukuruetal,“Cross-LayerWirelessBitRate
protocols proposed for wireless networks [6]. A common Adaptation,”inSIGCOMM,2009.
featureofmostoftheseschemesisthattheyavoidcollisions [3] K.Lin,N.Kushman,andD.Katabi,“ZipTx:
byutilizingcontrolframesorout-of-bandbusytones. These HarnessingPartialPacketsin802.11Networks,”in
schemes tend to be either quite conservative by reserving a Proc.ACMMobicom,2008.
largespacearoundthecommunicatingnodesordonotcom- [4] D.Halperin,T.Anderson,andD.Wetherall,“Taking
pletely eliminate the collisions. Some studies have shown thestingoutofcarriersense: Interferencecancellation
that enabling RTS-CTS reduces the overall throughput [7] forwirelesslans,”inMOBICOM,2008.
andhencedisabledbydefaultinmanydeployments[8]. [5] S.GollakotaandD.Katabi,“Zig-ZagDecoding:
CombatingHiddenTerminalsinWirelessNetworks,”
Recovering from Collisions: Apart from PPR mentioned inProc.ACMSigcomm,2008.
earlier, ZipTx [3] makes use of known pilot bits to detect [6] S.Kumaretal,“MediumAccessControlprotocolsfor
errorsandrecoverthepartialpackets. Wedonotinsertany adhocwirelessnetworks: Asurvey,”ElsevierAdHoc
known bits for detecting collisions. A receiver could apply Networks,vol.4(3),May2006.
interferencecancellation[4]torecovertheframeofinterest [7] Atheros,“802.11WLANPerformance,”.
bydecodingtheinterferingtransmissionfirstandthencan- [8] Broadcom,“WirelessLANAdapterUserGuide.,”.
celing it out. However, this approach works only when the [9] S.Rayanchuetal,“DiagnosingWirelessPacket
relativestrengthsofthesignalsatthereceiversatisfycertain Lossesin802.11: SeparatingCollisionfromWeak
thresholds. ZigZag decoding [5] is a form of interference Signal,”inINFOCOM,2008.
cancellation that recovers frames from repeated collisions. [10] JunPengetal,“AWirelessMACProtocolwith
While this is a creative approach, it requires that the same CollisionDetection,”IEEETransactionsonMobile
setofframesbeinvolvedinmultiplecollisions. Computing,vol.6(12),Dec2007.
6
TThhee aauutthhoorr hhaass rreeqquueesstteedd eennhhaanncceemmeenntt ooff tthhee ddoowwnnllooaaddeedd ffiillee.. AAllll iinn--tteexxtt rreeffeerreenncceess uunnddeerrlliinneedd iinn bblluuee aarree lliinnkkeedd ttoo ppuubblliiccaattiioonnss oonn RReesseeaarrcchhGGaattee..